The PoC smart contract is only good for someone who’d want to preemtively move his funds to a quantum-resistant address. Once QCs become available, you’d want a fork to enable safely migrating funds from any stranded and vulnerable contracts (including any non-standard variations of P2PKH, P2PKH, P2SH) where a commit-delay-reveal could work to prove original ownership.
Caveat with commit-delay-reveal is that miners could collude to steal, making a 51% potentially more damaging (right now, 51% could only censor transactions, or execute a double-spend fraud, but not out-right steal someone else’s funds) but once signatures are broken there’s no way around it but to use your P2PKH / P2SH address as an aged hashlock. With a long enough aging requirement, I think this would not be a deal-breaker.
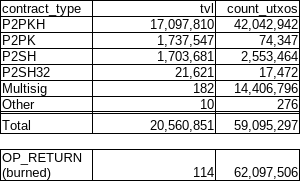
I don’t consider P2SH or P2PKH preimage to be breakable, so consideration here is just vulnerability of redeem scripts, where they’d become vulnerable only after exposing a vulnerable redeem script, same how P2PKH becomes vulnerable only after exposing the committed key.
With P2SH, it is more complex, because some contracts may already be quantum-resistant (signatureless covenants etc.), and only some would be vulnerable to QCs. Having a SF to require a commit for all of P2SH could inconvenience non-vulnerable contracts or could even break them (if contract requires a particular number of inputs & outputs and commitment would be provided by an additional input or output).
Therefore, I think a complete solution would be to extend the TX format so that this commit-delay-reveal happens “outside” the legacy TX, so that it doesn’t interfere with functioning of existing contracts and it would only be required for any script that executes OP_CHECKSIG, CHECKDATASIG, or CHECKMULTISIG with elliptic curve keys.