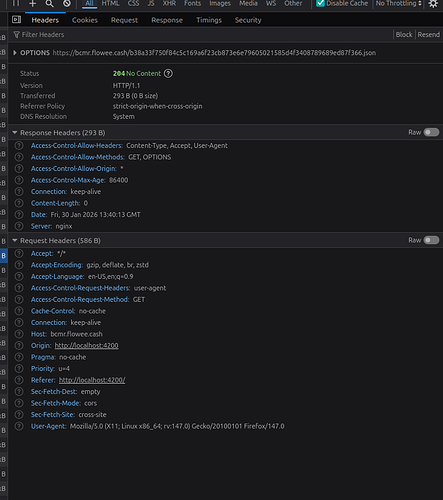
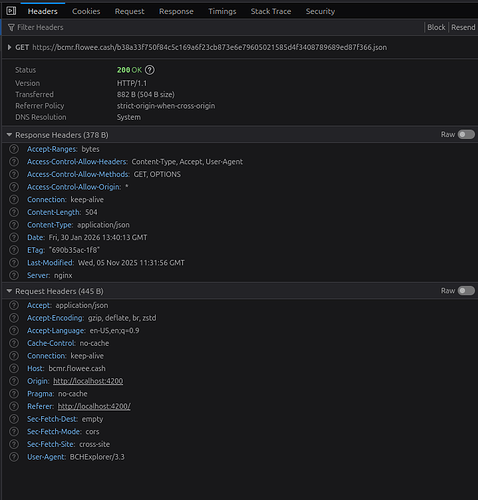
- Thanks for sharing the link with the code! And Flowee indexer so much faster than Paytaca indexer (no offense Joemar, if you are reading this)
- Got it, so it can be:
absent, marginal, good, high or ultimate
- I fully agree with the simplicity, don’t get met wrong… You still might want to hide the Nginx version though… (please add
server_tokens off; to your Nginx configs, for your own security).
I would like to come back again to CORS. Maybe I’m the first user that is using this indexer now from a javascript client (browser client)?
I like to help you by setting an User-Agent header on my side of the request, I do get it working now without it by sending a plain get request.
However, I think its better for you to also set a User-agent string from the client side. Allowing the server-side to identify the requests.
So I didn’t invented CORS, but the moment I would set a User-Agent header, a preflighted request will be done (out of my control). In in your case you can handle the OPTIONS requests and add the access-control-allow headers in the response, which will make the preflight request succeed.
Like you said, there is no “backend” but just a simple Nginx webserver. Which is fine, but that means you can configure CORS on the Nginx level.
I will use the “Basic NGINX CORS Configuration” from: NGINX CORS Configuration: The Complete Guide (2026) in this example, since once again keep it simple stupid (KISS).
I think the only thing I’m missing is this implementation in your Nginx config for your domain: http://bcmr.flowee.cash:
location / {
[....]
add_header Access-Control-Allow-Origin "*" always;
add_header Access-Control-Allow-Methods "GET, OPTIONS" always;
add_header Access-Control-Allow-Headers "Content-Type, Accept" always;
if ($request_method = OPTIONS) {
add_header Access-Control-Allow-Origin "*" always;
add_header Access-Control-Allow-Methods "GET, OPTIONS" always;
add_header Access-Control-Allow-Headers "Content-Type, Accept" always;
add_header Access-Control-Max-Age 86400 always;
add_header Content-Length 0 always;
return 204;
}
}
(Adapt the example I wrote for you to your own needs if you wish)
Thank you for helping. If you really really don’t want to support CORS, that is fine… but this not ideal. I won’t be able to set any HTTP headers.




 .
.