-
Summary
This CHIP proposes integrating Dandelion++ into Bitcoin Cash to strengthen transaction privacy and reduce traceability without requiring user reliance on extra tools like Tor or specialized wallets. By randomizing the path a transaction travels prior to full broadcast, Dandelion++ makes it significantly more difficult to pinpoint a transaction’s origin.
-
Motivation and Benefits
-
Reduced Traceability
- Dandelion++ first routes transactions (“Stem” phase) via randomized node paths. Only later does a node “Fluff” the transaction by announcing it broadly. This layered approach effectively obfuscates the transaction origin.
-
Lightweight, Node-Level Solution
- Operates at the networking layer, so no consensus changes or wallet modifications are needed. Users gain privacy benefits simply by running a Dandelion+±capable node.
-
Complement to Existing Privacy Tools
- Neutrino and Tor offer certain privacy improvements, but do not address entire-network correlation attacks. Dandelion++ tackles these root issues by ensuring transactions are well-masked before they propagate widely.
-
Technical Description
3.1 Dandelion++ Overview
- Stem Phase:- A newly created transaction is sent to one random peer, which relays it similarly, forming a random chain of “stem” hops.
- Fluff Phase:-
The node at the end of the stem path announces only the transaction hash (TxPoolInv). Nodes missing the transaction request it with RequestTxPoolTxs. This reduces redundant data transfers and further hides the origin.
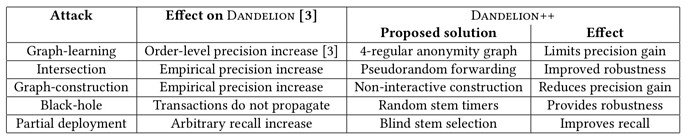
3.2 Comparison: Dandelion (BIP 156) vs. Dandelion++
The above table highlights how Dandelion++ improves upon the original Dandelion (BIP 156) as it was still exposed to various deanonymization attacks. Dandelion++ solved this by:
A. Randomized Relays: Transactions move through shuffled node paths during the Stem phase, making the true source harder to pinpoint.
B. Enhanced Network Topology: A more randomized structure prevents adversaries from easily mapping transaction flows.
C. Fail-Safe Mechanism: If any relay node fails, transactions automatically switch to the Fluff phase, avoiding long delays and preserving privacy.
- Specification
-
Node Configuration
-
A config flag such as enable_dandelionpp toggles this feature on/off.
-
Randomization parameters: e.g., refresh intervals for the anonymity graph.
-
-
P2P Messages
-
TxPoolInv <hash_list>: Announces transaction IDs instead of sending full data.
-
RequestTxPoolTxs <hash_list>: Requests the corresponding transaction blobs.
-
-
Stem Fail-Safe
- If the stem path stalls or times out, the node fluffs the transaction directly to avoid indefinite delays.
- Implementation Costs and Risks
-
Development Overhead
- Requires modifying node P2P logic to add new message types and random-forwarding rules.
-
Partial Adoption
- The anonymity set (and thus privacy) is stronger the more nodes participate. Early adopters see improvements, but full benefits emerge with wide adoption.
-
Latency Considerations
-
Empirical Data: Simulations in the Dandelion++ whitepaper demonstrate that transaction propagation had low latency increases compared to traditional broadcasting.
-
Additional round trips for requesting missing transactions during the fluff phase are rare due to efficient inventory broadcasting.
-
- Ongoing Costs and Risks
-
Maintenance & Testing
- Stochastic forwarding logic needs consistent integration testing to ensure correct behavior and performance.
-
Advanced Adversaries
- Even with Dandelion++, a global observer could attempt intersection attacks. Randomization, however, significantly raises the difficulty of tracing origins.
- Current Implementations
-
Reference Whitepaper & Proof of Concept:
Full Article: Dandelion++: Lightweight Cryptocurrency Networking with Formal Anonymity Guarantees - Empirical data can be found here for testing
-
Bandwidth Issues Discussions:
- Evaluation of Alternatives
-
Status Quo
- Simpler to maintain but offers less privacy. Leaves the network open to correlation attacks.
-
Original Dandelion (BIP 156)
- Provides some privacy improvements but lacks fail-safe mechanisms, advanced randomization, and robust adjacency mapping of Dandelion++.
-
Tor-Only or I2P
- More setup complexity and cannot alone prevent network-wide correlation attempts. Dandelion++ can complement these technologies.
- Pros, Cons & Limitations
-
Pros
-
Dandelion++ randomization reduces the likelihood of success.
-
No Consensus Impact : Doesn’t modify block validation rules. Security risk is minimal if carefully implemented.
-
As adoption grows, the protocol’s anonymity set improves, so earlier adopters benefit from subsequent uptake.
-
-
Cons
-
As seen there is still some problem with the fluff phase that might cause a delay in node propagation this issue can be seen in the reference I provided before in Monero here
-
Cannot fully eliminate sophisticated global surveillance.
-
- List of Major Stakeholders
-
Full Node Implementations (BCHN, BCHD, others)
-
Miners/Pools (transaction propagation concerns)
-
Exchanges & Payment Processors (customer privacy)
-
Wallet Providers (wallet changes not required, only node upgrade to the latest version)
-
BCH User Community (general interest in improved privacy)