It might be interesting to develop a security footprint scoring system, similar to VM computation budget.
For apps with organic engagement, the willingness to engage with the contract or “trust” appears to be inversely proportional to the length of the contract.
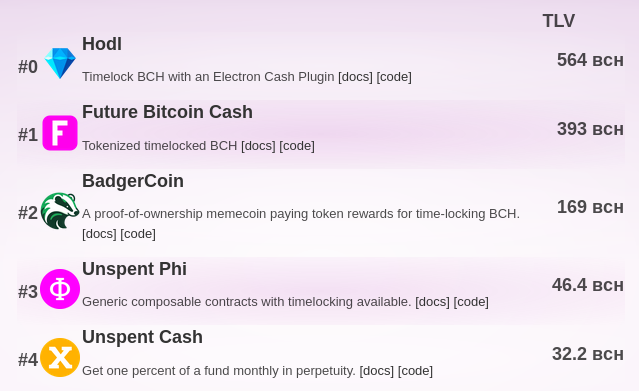
Below is a snapshot from a TLV tracker.
The unlockng bytecodes for the below dapps are 6, 34, 530, 53 bytes respectively.
So even through pat’s hodl app pays no yield, users are still trusting the much smaller contract more than a more complex contract.
Badger has also been offering consistently higher yields, but the vault much more complex than FBCH.